
ABAX has already some years ago Security in the IoT environment discussed. Due to the rapid development around digitalization it is time for an update.
In the third and last part of our series we deal with the special case of Smart Manufacturing.
Special case Smart Manufacturing - Never change a running system?
In the second part we discussed general topics around security for networked devices. In the third part of our series we turn to one of the most important industries that are intensively involved with Industry 4.0 and IoT, the production sector.
OT networks, which have been isolated up to now and have their own protocols, are increasingly being integrated into the company-wide IT network, as are other supply chain or distribution systems such as ERP systems. Of course, this has many advantages and is also one of the key features that make Industry 4.0 such as visibility, automation, feedback and real-time control.
The supply chain includes not only raw materials for manufacturing, but also third-party component suppliers, outsourced employees for non-core business activities and subcontractors to perform specific design, assembly, testing and distribution tasks. Each of these elements of the supply chain is a target
Industry 4.0 still has to learn IT security
The sweeping statement that production networks are more vulnerable to many types of security attacks is certainly not exaggerated. The special conditions of OT make it easier for potential attackers to overcome existing security systems:
OT are isolated and therefore automatically protected
Probably the most common assumption is that manufacturing networks operate in isolation from other areas (physical and logical) and are thus protected from external threats. Increasing networking, however, is increasingly counteracting this argument.
OT are excluded from normal IT routines
From a variety of founders, OT does not adhere so strictly to the usual IT routines for software updates and patching. Passwords for features often integrated by manufacturers, such as firewalls, often remain unchanged for years.
OT run on obsolete operating systems
According to a study by Trend Micro (as of December 2018), over 65 percent of industrial plants still use operating systems with Microsoft Windows 7 or older. These operating systems are no longer updated and thus represent a significant risk factor for plants.
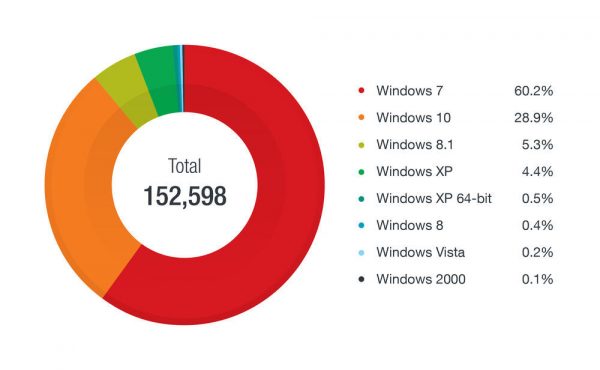
The most widely used operating systems in the manufacturing industry. Based on Trend Micro Smart Protection Network data for the period July to December 2018.
No one is an island
Unfortunately, OT networks also have weaknesses. This fact has of course not escaped attackers, as for example in the current Global Threat Intelligence Report 2020 by NTT is detected: the number of attacks on IoT systems is constantly increasing.
Additional explosiveness can result from the fact that installations which affect public infrastructure can also be affected, keyword Smart City or cases of hacked critical infrastructure, known as the cases of chopped Iranian nuclear power plant a few years ago or recently of the similar incident in India.
Most vulnerabilities concern interfaces such as HMIs (Human-Machine Interfaces), especially if these applications also have web access. This means that conventional web exploits are also dangerous and can be used as a means of attack.
And of course it must be mentioned again and again: the other side exploits all the weak points that are identified and acts in a highly professional manner.
Often seen as a problem: smooth integration of security measures
Digitization, especially in the manufacturing industry, is evident, for example, in the automation of production processes or the scaling of technical resources. Topics such as "artificial intelligence" and "machine learning" are omnipresent. At the same time, however, it can be observed that the structures in companies often do not keep pace with technological development.
An argument often quoted and put forward against a targeted focus on security measures around IoT and Industry 4.0 solutions is that these would disrupt the smooth running of processes, make them more complex for users or make them completely impossible.
Although these objections are understandable, they must not be used as an excuse to dispense with, or at least focus less on, the relevant security aspects surrounding networked systems. Especially the protection of (intellectual) company property, the prevention of dangers for employees and customers and the associated effects on affected companies should in themselves justify the necessary measures to take this aspect sufficiently into account when introducing and operating modern systems
Build confidence in connected devices
Despite all reservations, companies are well advised to take security seriously. This means that principles that have long been standard in classic IT systems must be adopted. Especially due to the fact that many OT systems have very long life cycles compared to IT systems, it is important to follow these instructions when upgrading, converting or expanding:
- Restrictions on rights at domain or network level are a suitable first step.
- This also includes generally restricting access authorizations.
- Furthermore, all access to confidential or protected information must be logged.
- In general, only those people who need to read, modify or create files should have access to file and resource information.
- Regularly removing or disabling unnecessary services can prevent potential security problems.
- A password policy is also useful to prevent outdated, insecure or lost access rights.
- The avoidance of outdated operating systems and regular system update routines to reduce vulnerabilities have already been addressed.
Further information about security around IoT
Conclusion: Understanding IoT security risks
The advantages of Internet of Things are undeniable. However, high-profile attacks combined with uncertainty about best security practices and the associated costs are keeping many companies from adopting the technology. End users are also concerned about the consequences of IoT security breaches. Confidence in the security of solutions is essential to realize the full potential of the Internet of Things. Digital security must be built into devices from the ground up and at all points in the ecosystem to prevent vulnerabilities in one part from compromising the security of the whole.
Modern IoT ecosystems are complex. Machines and objects in virtually every industry can be connected and configured to send data. The digital security risk is present every step of the way to the Internet of Things, and there are a number of hackers who would exploit a system's vulnerability. The first step for any IoT company is a thorough security risk assessment, which examines vulnerabilities in devices and network systems, as well as user and customer systems and any back-end systems involved. The risk must be mitigated for the entire lifecycle of the deployment, especially as it scales and expands geographically.
ABAX is available to answer your questions about Industry 4.0, IoT and of course also IoT Security of course would be very happy to help you.








