
IoT and Security - still up-to-date
The increasing digitalization and interconnection of systems offers opportunities, but also harbors risks (Picture: stock.adobe.com) A few years ago, ABAX already addressed the topic of security
a member of ROXCEL Group
Networked devices can give businesses a real boost with innovation, but anything connected to the Internet can be vulnerable to cyber attacks. From corporate servers to cloud storage, cybercriminals can find a way to attack systems in many places in an IoT ecosystem. So security is not a luxury but a must with any IoT project.
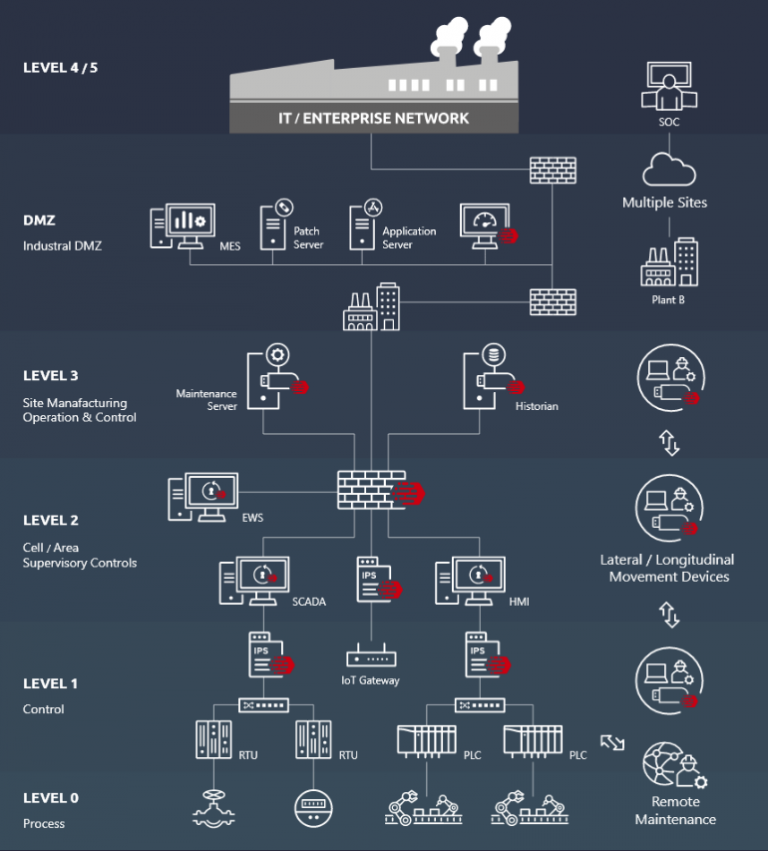
Especially in industries with systems that were previously separated from the "normal" IT landscape, i.e. classic OT (Operational Technology) environments, many new challenges around (cyber-) security arise. This is especially true in environments where the integration of protocols and devices that were not designed as part of a TCP/IP world (Transmission Control Protocol/Internet Protocol).
Innovative companies can better realize their potential with networked devices and new services, but they cannot ignore security concerns. As you build your IoT ecosystem, make sure your business, data and processes are protected and have a good cyber security plan in place.
We are happy to support and advise you about our solutions that meet your requirements.

The increasing digitalization and interconnection of systems offers opportunities, but also harbors risks (Picture: stock.adobe.com) A few years ago, ABAX already addressed the topic of security
OT networks that have been isolated up to now and equipped with their own protocols are increasingly integrated into the company-wide IT network. The special framework conditions of OT make it easier for potential attackers to overcome existing security systems: